28+ credit card use case diagram
Identity theft occurs when someone uses another persons personal identifying information like their name identifying number or credit card number without their permission to commit fraud or other crimesThe term identity theft was coined in 1964. A digital signature is a mathematical scheme for verifying the authenticity of digital messages or documents.

Amazon Com Modelones Gel Nail Polish Set 6 Colors All Seasons Retro Gel Polish Collection Black Green Brown Orange Nail Polish Set 2022 Fall Gel Nail Kit Soak Off Led Manicure Diy Salon
If you have many products or ads French.

. Real Estate for Rent. We will guide you on how to place your essay help proofreading and editing your draft fixing the grammar spelling or formatting of your paper easily and cheaply. It is a network of networks that consists of private public academic business and government networks of local to global scope linked by a broad array of electronic wireless and optical networking.
HM Treasury is the governments economic and finance ministry maintaining control over public spending setting the direction of the UKs economic policy and working to achieve strong and. Use case diagrams consist of 4 objects. Decentralized identifiers DIDs are a new type of identifier that enables verifiable decentralized digital identity.
The card was derived from the MultiMediaCard MMC and provided digital rights management based on the Secure Digital Music Initiative SDMI standard and for the time a high memory density. If the credit card is valid the order form will be processed by the system and checkout is complete. A valid digital signature where the prerequisites are satisfied gives a recipient very high confidence that the message was created by a known sender authenticity and that the message was not altered in transit Digital signatures are a standard element of most.
Only the Best and Brightest Can Meet 100 of your Expectations. 3 Persuasion Methods for Justification Essays. Most countries had introduced minimum wage legislation by the end of the 20th century.
The Domain Name System DNS is the hierarchical and decentralized naming system used to identify computers reachable through the Internet or other Internet Protocol IP networks. Containing 58 per cent of the world population in 2020 the EU generated a. This could be a person organization or an external system and usually drawn like skeleton shown below.
ASCII characters only characters found on a standard US keyboard. Since that time the definition of identity theft has been statutorily defined throughout both the UK. Promoting the car is expensive and engaging potential customers is ineffective.
A minimum wage is the lowest remuneration that employers can legally pay their employeesthe price floor below which employees may not sell their labor. The credit verification company is validating the credit card information. Its easy to use no lengthy sign-ups and 100 free.
As the theft of. A smart card chip card or integrated circuit card ICC or IC card is a physical electronic authorization device used to control access to a resourceIt is typically a plastic credit card-sized card with an embedded integrated circuit IC chip. Expert Academic Essay Writers.
Email addresses Myspace usernames and Myspace passwords for the affected Myspace accounts created prior to June 11 2013 on the old Myspace platform are at risk. 6 to 30 characters long. In 1999 SanDisk Panasonic Matsushita and Toshiba agreed to develop and market the Secure Digital SD Memory Card.
Professional Case Study Writing Help. Must contain at least 4 different symbols. Because minimum wages increase the cost of labor companies often try to avoid minimum wage laws by using gig workers by.
Find stories updates and expert opinion. The resource records contained in the DNS associate domain names with other forms of information. The European Union EU is a supranational political and economic union of 27 member states that are located primarily in Europe.
Use case Diagram of e-Commerce system Ship product. Leverage our proprietary and industry-renowned methodology to develop and refine your strategy strengthen your teams and win new business. After getting the order request sales clerk ships order product to customer within 5 to 6.
Get 247 customer support help when you place a homework help service order with us. Finding the 1010 Perfect Cheap Paper Writing Services. The EU has often been described as a sui generis political entity without precedent or comparison combining the characteristics of both a federation and a confederation.
The objects are further explained below. Carbon dioxide chemical formula CO 2 is a chemical compound made up of molecules that each have one carbon atom covalently double bonded to two oxygen atoms found in the gas state at room temperature. Actor in a use case diagram is any entity that performs a role in one given system.
As Close to 100 As You Will Ever Be. Many smart cards include a pattern of metal contacts to electrically connect to the internal chip. These are most commonly used to map human-friendly domain names to the numerical IP.
The Internet or internet is the global system of interconnected computer networks that uses the Internet protocol suite TCPIP to communicate between networks and devices. Latest breaking news including politics crime and celebrity. The radio frequency link establishes a connection to the switching systems of a mobile.
A microphone colloquially called a mic or mike m aɪ k is a transducer that converts sound into an electrical signalMicrophones are used in many applications such as telephones hearing aids public address systems for concert halls and public events motion picture production live and recorded audio engineering sound recording two-way radios megaphones and radio and. February 28 2022 HAU1430077. Reliable and very secure.
What are you waiting for. A mobile phone cellular phone cell phone cellphone handphone hand phone or pocket phone sometimes shortened to simply mobile cell or just phone is a portable telephone that can make and receive calls over a radio frequency link while the user is moving within a telephone service area. ピアスに関するqa 販売しているピアスはすべて2個売りですか ピアスは2個売りとなっております 一部の特殊な形状のピアスや片耳用のピアスは1個売りとなっております.
Use Case Diagram objects. For all your credit or financing needs we offer our services. 15 Qualities of the Best University Essay Writers.
In the air carbon dioxide is transparent to visible light but absorbs infrared radiation acting as a greenhouse gasIt is a trace gas in Earths atmosphere at 417. Your credit card details will not be shared with SDN. 90 case studies are matching your searchfilter criteria.
A DID refers to any subject eg a person organization thing data model abstract entity etc as determined by the controller of the DIDIn contrast to typical federated identifiers DIDs have been designed so that they may be decoupled from centralized registries. The team already possessed AI technology capable of interacting with people in a personalized way. As you know Myspace does not collect use or store any credit card.
It was designed to.
2
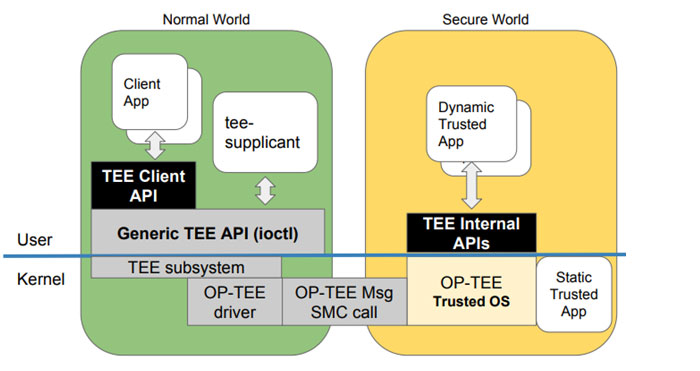
Trusted Software Development Using Op Tee Timesys
2
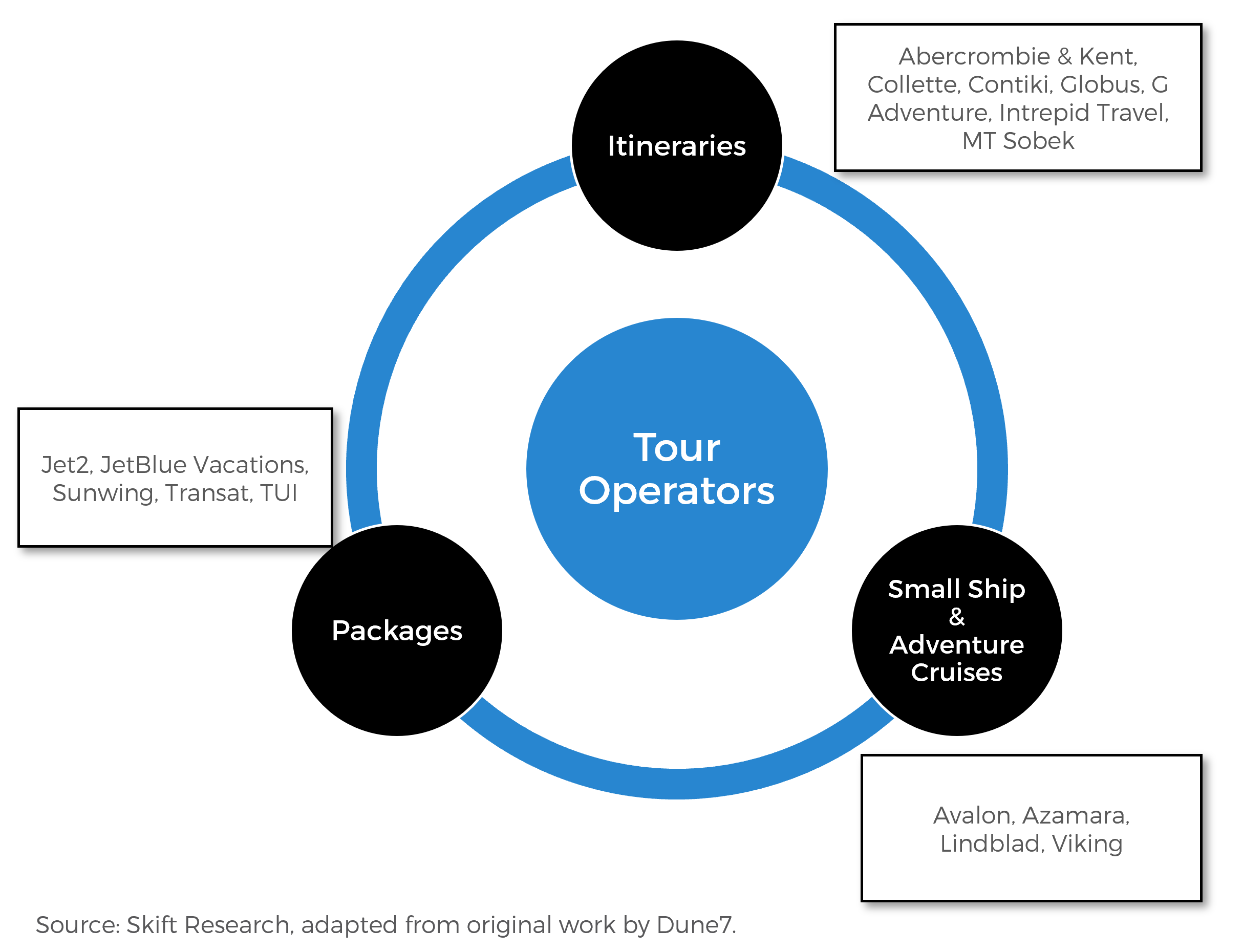
Multi Day Tour Operators 2021 Reshaping Supply Chains And Distribution

Ex 99 1
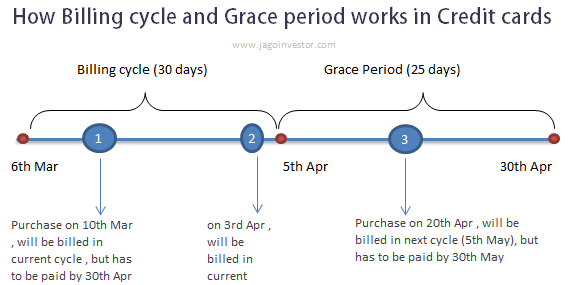
Minimum Balance In Credit Card How Does It Work
Do You Think You Waited Too Long To Get Married Quora
Why Aren T Manholes Square Quora
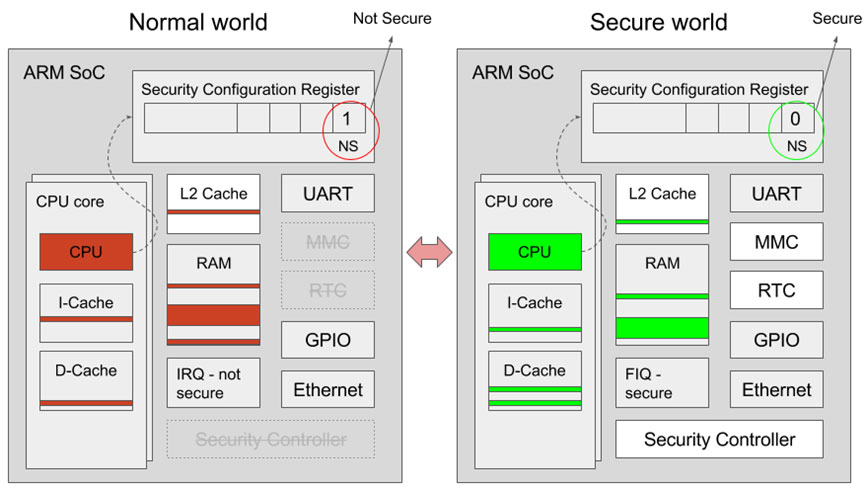
Trusted Software Development Using Op Tee Timesys

Security And Privacy In Unified Communication Acm Computing Surveys

Security And Privacy In Unified Communication Acm Computing Surveys

Kidde 10 Year Worry Free Plug In Carbon Monoxide Detectors For Hallway Kitchen And Living Room 3 Pack Kn Cop Dp 10yr The Home Depot
2
2
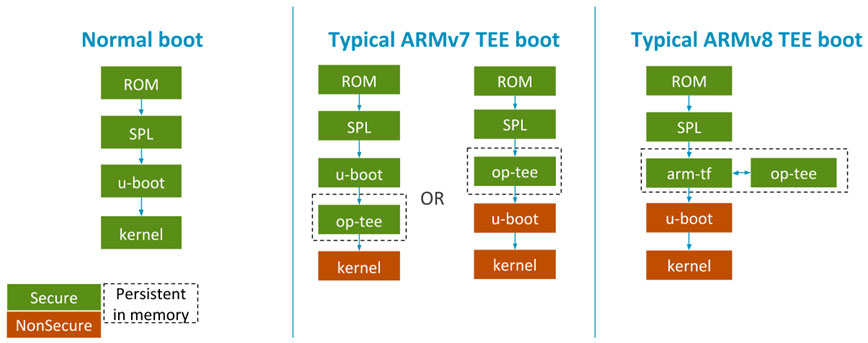
Trusted Software Development Using Op Tee Timesys
How Long Does It Take A 4 Inch Slab Of Concrete To Dry Quora

Mermaid Scale Digital Paper Rainbow Glitter Mermaid Scales Etsy Mermaid Wallpapers Mermaid Wallpaper Backgrounds Pink Glitter Wallpaper